Which of the Following Are Symmetric Encryption Algorithms
AES Which of the following is an asymmetric algorithm. 3DES RSA ECC MD5 Correct Answer The Correct Answer for this Question is 3DES Explanation.
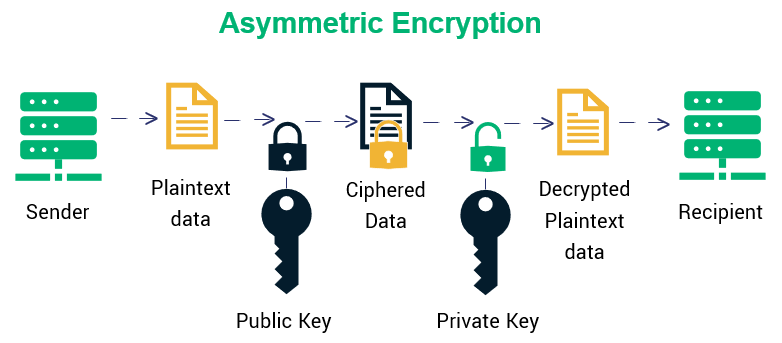
Types Of Encryption What To Know About Symmetric Vs Asymmetric Encryption Infosec Insights
Is given below Which of the following is a symmetric encryption algorithm.

. Sign up for your free Skillset account and take the first steps towards your certification. Symmetric encryption is one of the oldest and best-known technique which makes use of secret key that could be a. Select 3 choices A.
Symmetric key encryption has been the main form of cryptography for a long time. Encryption types can be easily divided into these two categories. Other examples of symmetric encryption algorithms include International Data Encryption Algorithm IDEA Skipjack and Blowfish.
Common symmetric encryption algorithms include all of the following except _____. Symmetric encryption algorithms are used combined with an encryption key to do two main things. Symmetric encryption is also known as secret key encryption.
For banking-grade encryption the symmetric keys must be created using an RNG that is certified according to industry standards such as FIPS 140-2. When the same keys are used during both encryption and decryption the algorithm is said to be symmetric. Which of the following are symmetric cryptography algorithms.
The option that best explains how symmetric encryption are typically used is. Here are some of the most common types of Symmetric-key algorithms. RC4 AES DES 3DES QUA.
Common Symmetric Encryption Algorithms AES Encryption or Advanced Encryption System. DSA Show Answer Post navigation Previous question Next question Leave a Reply. Cryptography is the study of different techniques to secure data from an unauthorized entity.
To establish standards pertaining to their functions and acceptable use. Because digital signatures are so important in proving who sent which messages the US. It is a type of encryption that uses the same secret key for encryption and decryption.
It requires more resources than asymmetric encryptionD. Set lengths of bits are encrypted in blocks of electronic data with the use of a specific secret key. Cisco 210-250 v2 Tags.
DSA and ECC are asymmetric encryption algorithms. Symmetric encryption uses a single key that should be kept secret. Correct Answer for the Question Which of the following is a symmetric encryption algorithm.
Most of the cryptography involves very advanced Mathematical functions used for securing data. Admin December 11 2017 Which of the following are symmetric encryption algorithms. There are two types of symmetric encryption algorithms.
Stream cipher Hashing Which of the following are symmetric algorithms. Which of the following areas is considered a strength of. DiffieHellman DH Digital Signature Algorithm DSA and Elliptical Curve Cryptography ECC are asymmetric algorithms.
The following algorithms use Symmetric Encryption. DH is an asymmetric key exchange method. AES is the symmetric algorithm-of-choice for most applications today and is very widely used mostly with 128 or 256-bit keys with the latter key length even considered strong enough to protect military TOP SECRET data.
In computer science we try to develop strategies and practices for protecting sensitive data. Convert the ciphertext back to plaintext. Symmetric Encryption Cryptography in Java.
It uses a public key and a private key to encrypt and decrypt trafficC. Which of the following can be classified as a stream cipher. Which two characteristics of symmetric encryption are true.
Which of the following are examples of symmetric block. AES is one of the most common symmetric encryption algorithms used today developed as a. Convert readable text plaintext into unreadable encrypted text ciphertext.
Which of the following encryption mechanisms offers the least security because of weak keys. DES Data Encryption Standard Data encryption standard is a form of block cipher which encrypts data in 64-bit chunks or blocks by using just one key that comes in three different sizes 192-bit 128-bit and 64-bit keys. Name all that apply.
Symmetric encryption is fast and efficient when compared to Asymmetric Encryption. Which of the following Algorithms not belong to symmetric encryption S Cyber Security. Which of the following algorithms are used in symmetric encryption.
A few popular symmetric encryption algorithms are Twofish Blowfish DES Triple-DES AES etc. It is an asymmetric key algorithm. It uses digital certificatesB.
When sending messages using symmetric encryption which of. Digital Signature Standard DSS is not a symmetric key algorithm. Select two 3DES Blowfish.
Symmetric encryption which is single-key encryption and asymmetric encryption or public-key encryption. It is faster than asymmetric encryptionE. Which of the following are examples of symmetric encryption algorithms.
The number of rounds varies with key length. In 1991 NIST proposed a federal. It uses the same key to encrypt and decryptContinue reading.
Symmetric encryption algorithms use the same encryption key for both encryption and decryption. Blowfish ECC AES RSA DES Diffie Hellman Explanation. Frequency hopping spread spectrum is a method of transmitting radio signals by rapidly changing the carrier frequency and is controlled by the codes known to the sender and.
Which of the following is true about heuristic-based. The same key is used for both encryption and decryption of data.

What Is Symmetric Key Cryptography Encryption Security Wiki

Symmetric And Asymmetric Encryption By Rafael Almeida Hackernoon Com Medium
Apa Sih Cryptography Itu Yuk Pahami Lebih Jauh Coding Studio
No comments for "Which of the Following Are Symmetric Encryption Algorithms"
Post a Comment